
FuruCombo (COMBO) is an integral Ethereum-based DeFi product focused on building "combos," Lego-like constructions that allow users to use multiple instruments for liquidity provision and decentralized exchange. Today, it was drained for $14,000,000—and it is not alone.
Fake AaveV2 has stolen FuruCombo's liquidity
Today, in the early morning hours, FuruCombo (COMBO) informed its users that one of the parts of its ecosystem was compromised. All affected elements were immediately deauthorized, and FuruCombo told its customers to move their tokens.
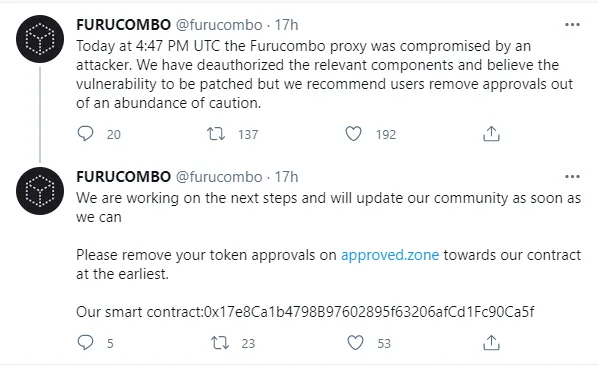
Then, the team admitted that $15 million in various assets are inaccessible, so FuruCombo is going to unveil a "mitigation plan." Some users have lost hundreds of thousands of dollars, according to their Twitter comments.
Cryptocurrency researcher Igor Igamberdiev, well known for his brilliant reviews of the attacks against DeFis, reported that an attacker made FuruCombo (COMBO) instruments to treat the impersonator contract as a new implementation of the AaveV2 protocol.
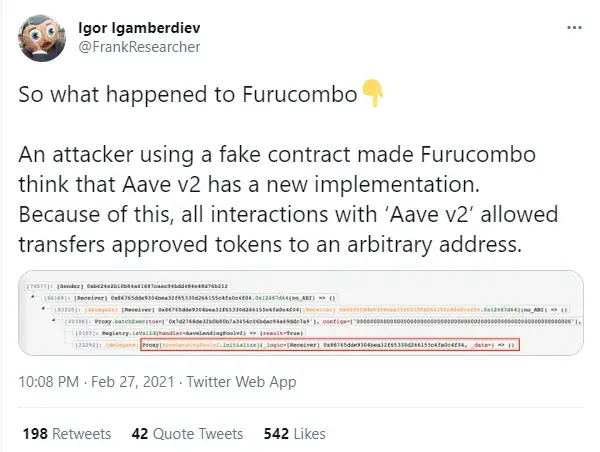
According to Mr. Igamberdiev, hackers hijacked funds for 21 assets worth more than $14 million at the time of the attack.
Beware of "social engineering"
Two weeks ago, on Feb. 13, 2021, CREAM DeFi's project IronBank lost more than $37,500,000 due to a flash-loan attack that affected five protocols.
At the same time, ArmorFi (ARMOR), a multi-purpose DeFi protocol, reported an attack with an unusual design. According to its official statement, hackers used the "social engineering" method to steal Armor's funds.
An attacker impersonated an influential OTC investor at Discord. It reached two members of the ArmorFi team in order to close transactions in a rush. One of the "non-dev" team members was chosen as escrow. Then, attackers sent fake proof of finalized transactions revealing his negligence:
He did not follow basic OpSec to verify transactions.
As a result, more than 600 Ethers found their way into scammers' pockets. Meanwhile, some commenters on Crypto Twitter suspect a "rug pull." Analyst Taha Zafar noticed that ArmorFi did not prepare an ICO or a private sale, so the whole story about large-scale OTC deals looks "funny" to him.

 Caroline Amosun
Caroline Amosun Tomiwabold Olajide
Tomiwabold Olajide Dan Burgin
Dan Burgin Gamza Khanzadaev
Gamza Khanzadaev Arman Shirinyan
Arman Shirinyan