The decentralized exchange CrediX_fi has suffered a devastating security breach, with attackers draining an estimated $4.5 million from multiple pools. The exploit originated from a compromised admin account ending with 662e, which held dangerously broad permissions across the protocol: including POOL_ADMIN, BRIDGE, ASSET_LISTING_ADMIN, EMERGENCY_ADMIN and RISK_ADMIN.
Hack's origin
By siphoning off assets and minting unbacked acUSDC tokens, a synthetic asset unique to CrediXs Sonic USDC market, the attacker planned the theft using the BRIDGE role. Without any support or collateral, the hacker was able to borrow and drain pool assets using this minting exploit, essentially creating money out of thin air.
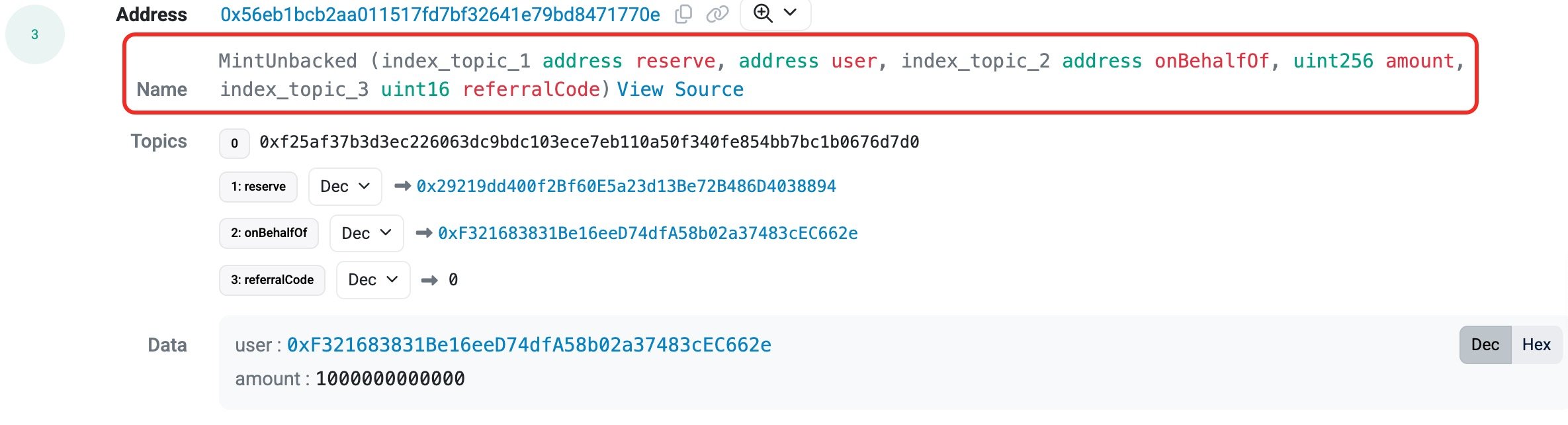
As a result, one of the mechanisms of the protocol suffered a breach. CrediX has disabled its website in response, advising users to withdraw using only smart contracts. Due to the protocol's lack of backup infrastructure to isolate or quarantine compromised permissions, this extreme measure emphasizes how serious the situation is. This means uncertainty and damage control for investors and users.
Roles compromised
Major roles have been compromised, the protocol is now seriously compromised and developers have not been transparent about remediation audits or a recovery roadmap. Investors should expect long-term consequences. CrediX pool's liquidity is probably going to disappear. acUSDC and any governance or utility tokens associated with the protocol are in danger of collapsing due to the severe erosion of token trust.
Developers lose trust in the integrity of the smart contracts and role management even if they regain control. An address that can act as a god across several systems turns the ecosystem into a single point of failure. Investors should avoid any further CrediX-related exposure until complete transparency, on-chain forensics and third-party audits are provided.



 Dan Burgin
Dan Burgin Vladislav Sopov
Vladislav Sopov