
Disclaimer: The opinions expressed by our writers are their own and do not represent the views of U.Today. The financial and market information provided on U.Today is intended for informational purposes only. U.Today is not liable for any financial losses incurred while trading cryptocurrencies. Conduct your own research by contacting financial experts before making any investment decisions. We believe that all content is accurate as of the date of publication, but certain offers mentioned may no longer be available.
In the rush to fully decentralize rollups, Vitalik Buterin has shared an important reminder that is easy to forget: stage 2 is not always more secure unless the underlying proof system is impenetrable. He clarified in a post, presenting a condensed mathematical model, that moving too quickly to stage 2 without appreciably enhancing proof robustness could actually raise the failure rate.
The model makes the following assumptions: safety and liveness failures are equally likely, and each member of the security council has a 10% independent failure chance. A 4-of-7 multisig is used in stage 0 and a 6-of-8 is used in stage 1. The likelihood that the proof system will break varies. As the proof system's failure probabilities increase, the findings indicate that stage 0 or stage 1 provide more security than stage 2.
Only when the proof system is incredibly dependable (e.g., stage 2 is the best option if the failure rate is 10⁻⁵ or less. Moving to stage 2 with an undeveloped or centralized proof system is the worst possible setup, as Buterin points out, since it combines the risks of both. He also points out how this model does not always apply in the real world, where council members frequently experience common mode failures, collusion vulnerabilities in shared infrastructure or legal coercion, which makes multisig setups less effective in practice than the model suggests.
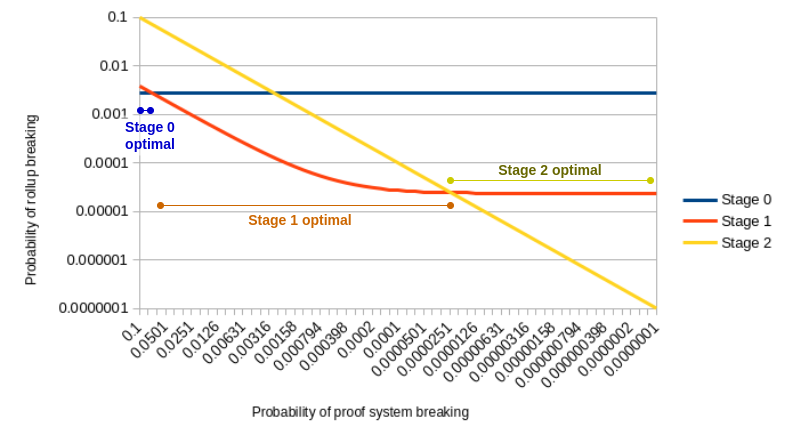
Even so, a strong proof system is necessary for stage 2 to be safer. Buterin suggests employing proof system multi-sigs, which combine several separate proof systems as a temporary measure to reduce these risks. According to him, stage 2 is not the only thing that matters. In addition to the rollups, decentralization phase ecosystem tools such as l2beat should monitor the maturity of proof system audits. Achieving true security involves a gradual alignment of governance and cryptographic integrity; it is not a checkbox.


 Dan Burgin
Dan Burgin Vladislav Sopov
Vladislav Sopov