Zero-knowledge proof (ZKP) systems require both the ‘Prover’ and ‘Verifier’ to construct and verify a proof of the original problem using logical circuits. With the increasing adoption of ZKP-based Layer 2 protocols like zkSync and Scroll, and public chains like Filecoin and Aleo that rely on transaction witnesses, combined with the growing number of anonymous coin projects built on ZKP, the integration of ZKP and blockchain presents complex security challenges.
This article aims to identify potential vulnerabilities that may arise from the combination of ZKP and blockchain from a security perspective. By doing so, it provides a valuable resource for security teams working on ZKP projects.
Three Pillars of ZK-Proofs’ Security: Basics
When analyzing the security of a system, it's essential to first examine its characteristics to ensure that all security services meet the requirements of the system. A zero-knowledge proof system must fulfill the completeness, soundness, and zero-knowledge properties of the proof system itself.
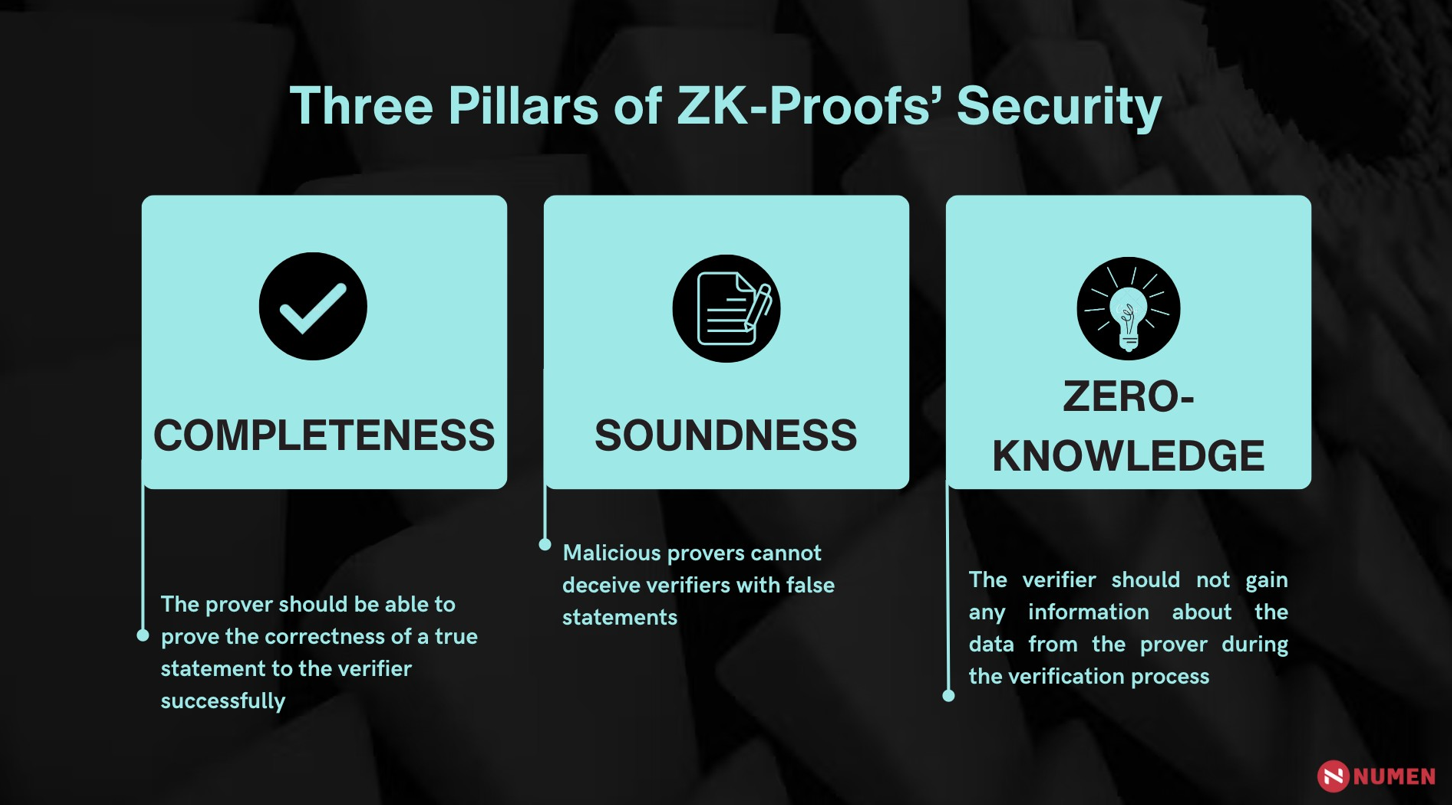
- Completeness: The prover should be able to prove the correctness of a true statement to the verifier successfully.
- Soundness: Malicious provers cannot deceive verifiers with false statements.
- Zero-knowledge: The verifier should not gain any information about the data from the prover during the verification process.
If a proof system lacks completeness, it may fail to provide correct proof under extreme conditions, resulting in a denial-of-service state. If a proof system lacks soundness, attackers can forge proofs or create special proof structures to deceive verifiers, leading to severe permission bypass issues.
If a zero-knowledge proof system fails to satisfy zero-knowledge, it may leak original parameters during the interaction process, enabling attackers to construct attack proofs based on leaked data or cause malicious behaviour by the prover.
What are specific security concerns associated with ZK-proofs?
For blockchain projects based on ZKP protocols, there are a number of important security considerations to focus on.
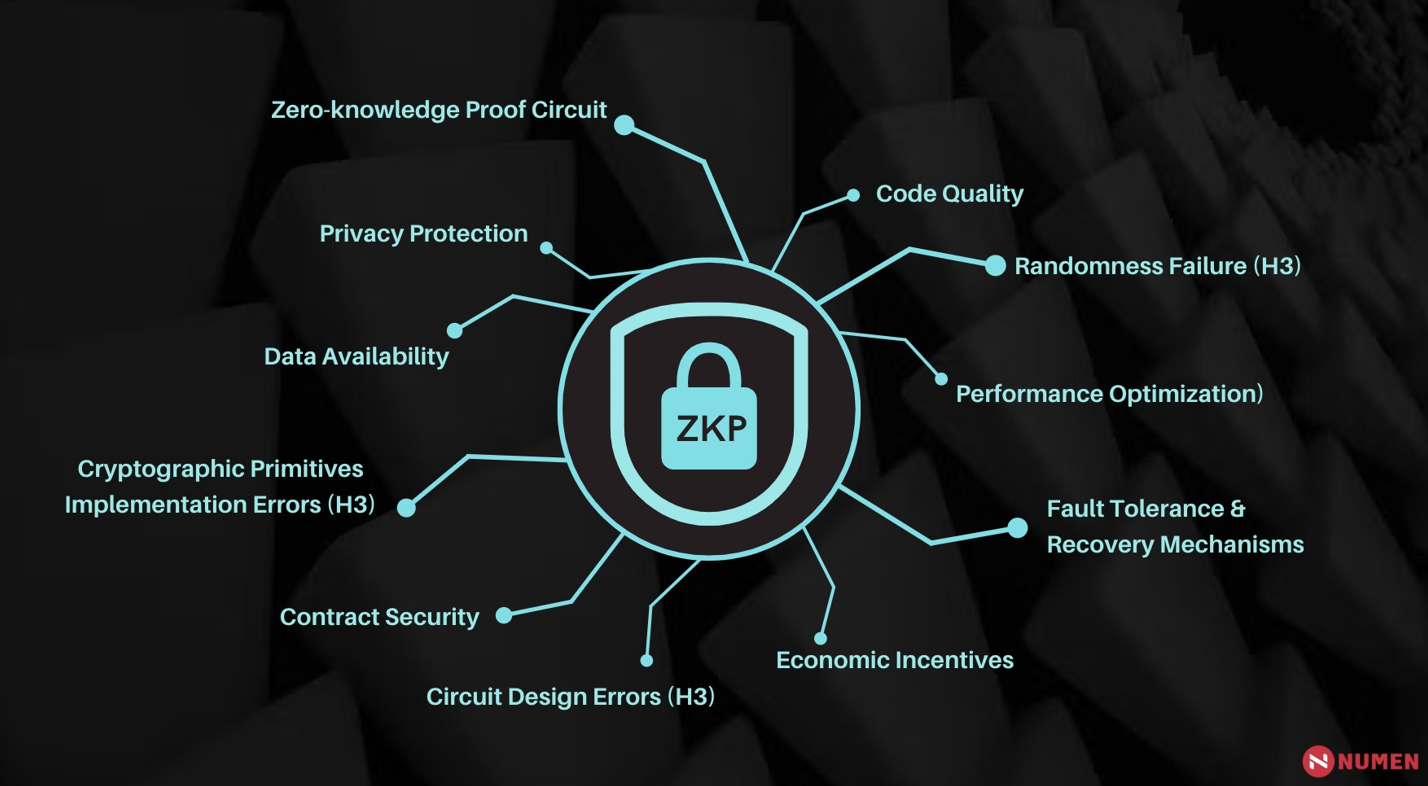
Zero-knowledge proof circuit
Ensuring the security, effectiveness, and scalability of the ZKP circuit used in a project is crucial. This involves a focus on several key areas, including circuit design, cryptographic primitive implementation, and protection of randomness. By carefully considering each of these factors, project teams can help to mitigate potential vulnerabilities and ensure the overall robustness of their ZKP system.
Currently, detecting errors in ZKP circuit design is a challenge due to the lack of reliable tools available. This can lead to the introduction of logic errors during the design process, which in turn can compromise the security properties of the proof process, including completeness, soundness, and zero-knowledge.
For example, during the 2018 Zcash Sapling upgrade, a circuit design flaw was identified that could have allowed for the unlimited counterfeiting of ZEC tokens. Although this vulnerability was not exploited, it highlights the potential seriousness of circuit design errors in ZKP systems.
The correctness and security of a ZKP circuit relies heavily on the proper implementation of cryptographic primitives, including hash functions, encryption algorithms, and more.
However, even a small error in the implementation of these primitives can compromise the security of the entire proof system.
This issue is not unique to ZKP-proof systems, as evidenced by the vulnerability in BNB Chain's Merkle tree validation primitives, which resulted in a loss of $586 million. It is crucial for developers to pay close attention to the implementation of cryptographic primitives and regularly audit their code to ensure the security of their systems.
Zero-knowledge proof typically relies on a random number generator (RNG) to generate random numbers. If there are problems with the random number generation process, it may compromise the security of the proof. For example, in 2018, the Dfinity development team discovered a random number generation vulnerability while auditing its zk-SNARK-based privacy scheme. This vulnerability could allow an attacker to crack the zero-knowledge characteristics of the circuit with specific inputs.
Contract security
This is mainly aimed at Layer2 or privacy coin projects implemented through smart contracts. Smart contract security is self-evident. In addition to common vulnerabilities such as re-entrancy, injection, overflow, and permission bypass, for ZKP projects, smart contracts play a critical role in asset cross-chain and proof verification. Vulnerabilities in cross-chain message verification and proof verification can directly lead to the failure of reliability. For example, earlier this year, a Circom Verify contract vulnerability was discovered, directly leading to the implementation of double spending with false names.
Data availability
Check how the project solves the problem of data availability to ensure that off-chain data can be accessed and verified securely and effectively when needed. The focus should include data storage, verification mechanisms, and transmission processes.
Economic incentives
Evaluate the incentive mechanism in the project to ensure that it can stimulate verifiers, users, and other participants to participate and maintain the security and stability of the entire system. The focus should include incentive model design, reward distribution, and punishment mechanism.
Privacy protection
If the project involves privacy protection, audit the implementation of its privacy scheme. Ensure that user data is adequately protected during transmission, storage, and verification while maintaining system availability and reliability. Although zero-knowledge proof requires the introduction of complex concepts such as simulation and rewind, we can still infer whether the privacy of the prover has been leaked based on the protocol communication process. For malicious verifiers, we can also infer the possibility of reconstructing the prover based on the content of their interaction data.
Performance optimization
Evaluate the performance optimization strategies in the project, such as transaction processing speed and verification efficiency. Audit the optimization measures in the code implementation to ensure that the project can meet performance requirements.
Fault tolerance and recovery mechanisms
Audit the project's fault tolerance and recovery strategies in case of unexpected situations, such as network failures or malicious attacks. Ensure that the system can automatically recover and maintain normal operation when possible.
Code quality
Audit the overall quality of the project's code, focusing on code readability, maintainability, and robustness. Evaluate whether there are any issues with non-standard programming practices, redundant code, potential errors, and other problems.
How can ZKP projects be secured?
When it comes to Zero-Knowledge Proof (ZKP) projects, there are important security considerations that must be taken into account by project teams and users alike. One option for achieving comprehensive security protection is to engage the services of a Web3 Security company such as Numen Cyber. This company has extensive experience in auditing smart contract codes and is also proficient in auditing circuit coding logic to ensure the accuracy of constraint conditions and witness generation through both manual and automated methods. Their expertise in detecting under-constrained computation vulnerabilities, simulating multiple attack behaviours, and assembling custom logic witnesses for critical logic is particularly noteworthy.
Numen Cyber also provides fuzzing and security testing capabilities for sequencer/prover code and verification contracts, offering protection for both node entities and node data. In addition to security services, Numen Cyber has developed two security products that can provide real-time protection for projects after they go online:
ImmunX is a state-of-the-art Web3-based security monitoring and protection system that is designed to sense security situations, issue risk alerts, and track on-chain activities. When used in conjunction with Sequencer, Numen Cyber can provide attack-blocking services on Layer 1 blockchains, providing an additional layer of protection for sensitive projects. Numen
Cyber has already collaborated with Binance to improve risk awareness and protection for BNB Chain.
Leukocyte is a powerful host security protection product that incorporates cutting-edge CWPP and ASA capabilities. It is designed to protect cloud hosts, physical hosts, and virtual machines by providing closed-loop management of assets, risk, threats, and responses for servers. This ensures that all servers are kept secure and operating reliably, regardless of the potential threats they may face.
Conclusion
By highlighting these security considerations, Numen Cyber provides a valuable resource for security teams working on ZKP projects. To properly address the security of ZKP projects, it's important to identify the specific context in which ZKP is being used, as the security considerations for Layer 2, privacy coins, and public chains may vary. Nonetheless, regardless of the use case, it's imperative to prioritize the three essential properties of ZKP: completeness, soundness, and zero-knowledge.


 Dan Burgin
Dan Burgin Vladislav Sopov
Vladislav Sopov