
Independent Japanese Ethereum researcher and developer Kikx claims that the Ethereum (ETH) Programmatic Proof-of-Work (ProgPoW) algorithm fails to protect the second blockchain from ASIC-based mining. What does this mean and why is it of crucial importance to Ethereum?
No ASIC-resistance in ProgPoW
According to Kikx, the hash-function code operated by the ProgPoW algorithm can be modified in order to allow the application-specific integration circuits to take part in its mining. And this is definitely a feature ProgPoW was designed to erase from the network.
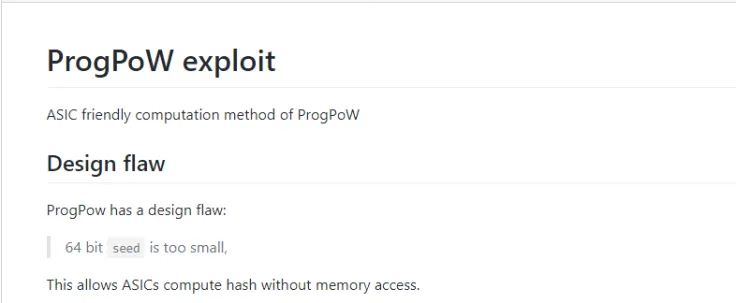
Kikx noticed that the 64 bit ‘seed’ (one of the inputs in Ethereum (ETH) computations) is too small, which allows ASICs to compute hash without accessing the memory. As a result, the owners of ASICs can modify the code in three simple steps and gain superiority in mining profitability.
Kikx was generous enough to share all of his suggestions (the nature of the flaw, vulnerable areas of the code as well as a live demo of a possible execution) in his GitHub
Developers Embarrassed
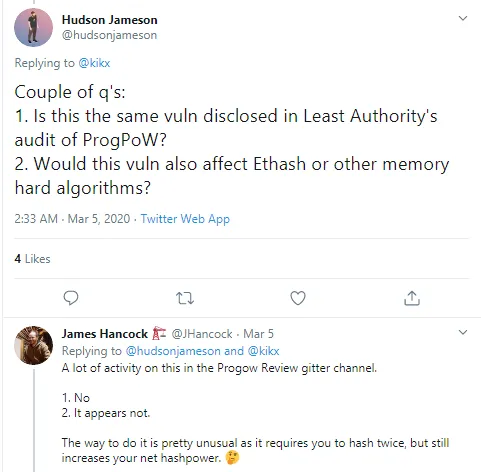
Top Ethereum (ETH) developers, e.g. Hudson Jameson and James Hancock, discussed Kikx' conclusions, the latter of whom found the vulnerability ‘pretty unusual’ and not constituting a danger to other mining algorithms.
In addition, Kristy-Leigh Minehan, author of mining algorithms, highlights that:
This is a pretty cool trick - though we have yet to confirm it works in practice
Advertisement
Programmatic Proof-of-Work is a mining algorithm that was intended for eliminating the possibility of mining Ethereum (ETH) on ASICs in order to ensure the safety and decentralization of the network. It has been criticized due to the possibility of an unwanted hard-fork. Also, its implementation may result in delay with the launch of Ethereum (ETH) 2.0.
 Arman Shirinyan
Arman Shirinyan Alex Dovbnya
Alex Dovbnya Denys Serhiichuk
Denys Serhiichuk