Noctura today introduced a compliant, zero-knowledge privacy protocol built natively on Solana, designed to deliver confidential transfers without forcing users, exchanges, or institutions into an “all-or-nothing” tradeoff between privacy and regulatory survivability. According to the project’s technical whitepaper, Noctura combines a shielded state layer (commitments, nullifiers, and Merkle roots anchored on Solana) with a dual-mode wallet that lets users operate transparently for full DeFi/NFT composability, or switch into shielded mode for private value transfer when confidentiality is needed.
Why this matters: transparency has become a risk surface
Public ledgers are excellent for auditability, but they also create persistent exposure: treasury movements can be tracked, counterparties can be mapped, and trading strategies can be inferred. For funds, DAOs, and teams running large on-chain operations, the “always-public” default has evolved from a feature into an operational liability. Noctura’s thesis is straightforward: if Web3 wants mainstream adoption and institutional participation, privacy must be usable, verifiable, and selectively disclosable, not an opaque black box that breaks integrations or triggers compliance friction.
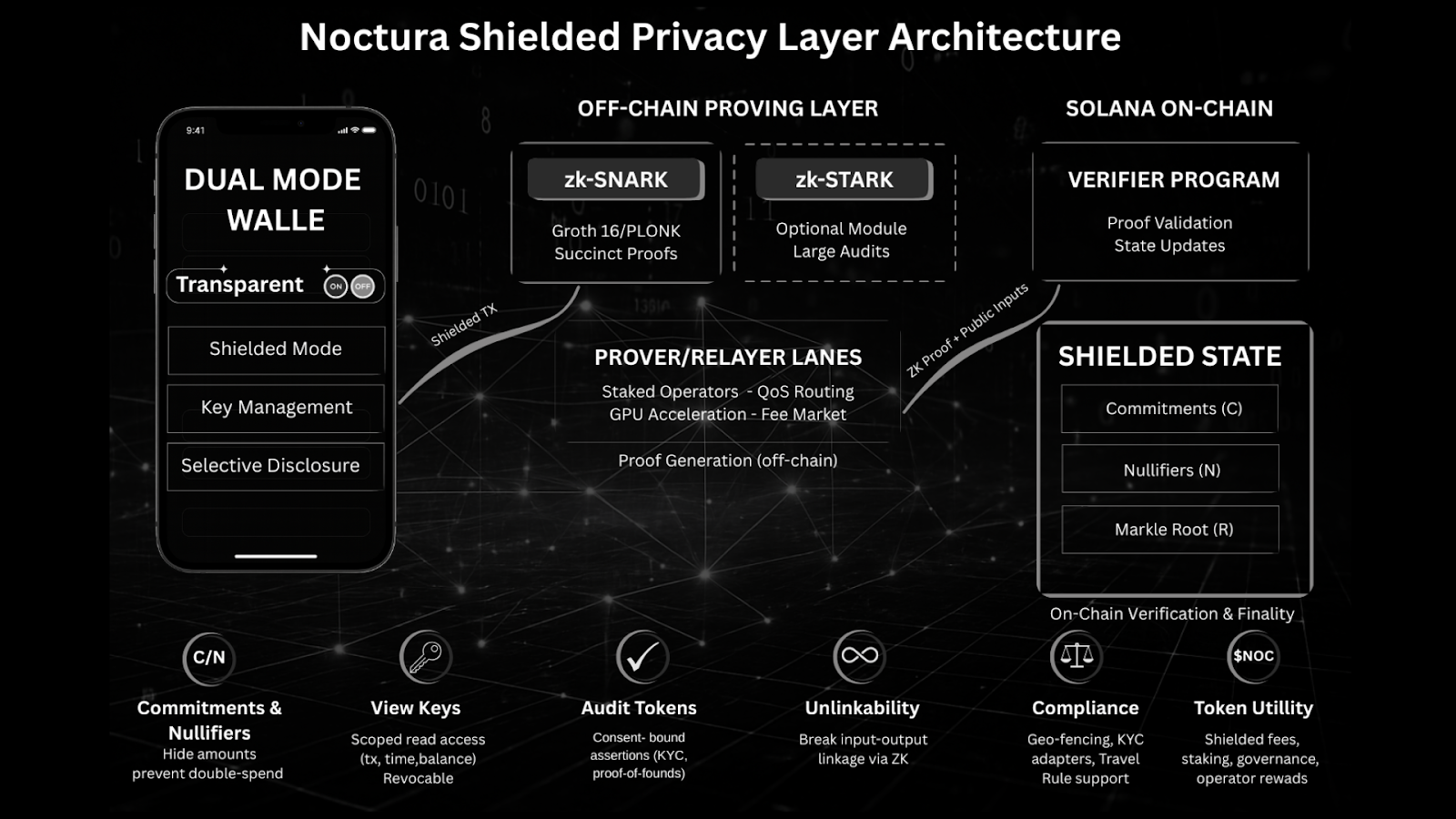
Architecture: off-chain proving, on-chain finality
Noctura is not a sidechain or rollup. The core design keeps heavy computation (proof generation) off-chain, while leveraging Solana for on-chain verification and finality. In practice, shielded transfers update an on-chain state machine defined by:
- Commitments (C): cryptographic bindings for notes (value + recipient + randomness)
- Nullifiers (N): one-time markers preventing double spends without revealing which note was spent
- Merkle root (R): the canonical commitment tree root anchored on Solana
Users (or delegated prover lanes) generate zk proofs to show membership, non-replay, and balance conservation; a lightweight Solana verifier program checks the proof and atomically updates state. This structure allows privacy guarantees (sender/receiver/amount confidentiality and unlinkability) while retaining Solana’s execution environment and ecosystem connectivity.
“Selective disclosure” built for listings and real counterparties
A defining component of Noctura is its compliance posture: instead of blanket transparency or blanket secrecy, the wallet introduces user-consented, scoped disclosure primitives:
- View Keys: read-only access constrained by transaction IDs, time windows, or balance thresholds, designed to be revocable and limited in scope
- Audit Tokens: short-lived, consent-bound credentials that can prove specific facts (e.g., proof-of-funds or a KYC pointer hash) without exposing an entire transaction graph
This approach targets practical workflows: exchange onboarding, OTC settlement, treasury attestations, vendor payments, and audit requests, where counterparties often need evidence, but not total surveillance.
$NOC utility and investor thesis
The $NOC token is designed as the protocol’s operating fuel and incentive mechanism. In the whitepaper, $NOC is positioned to power shielded transaction fees, support staking and governance, and align operator behavior for prover/relayer lanes through staking and slashing incentives. The token supply is fixed at 256,000,000 $NOC, with allocation including community distribution via presale, staking rewards, liquidity provisioning, marketing, team lockups, and reserve for upgrades.
Security process as a product feature
Noctura frames security as ongoing operations, not a one-time milestone: circuit reviews, verifier audits, bug bounties, incident response playbooks, and guarded upgrades with governance controls are described as core requirements for credible privacy infrastructure, particularly when the target users include funds, enterprises, and regulated venues.
For investors tracking the privacy category, Noctura’s positioning is clear: Solana-native performance rails, a wallet-first adoption funnel, a SNARK-first verification strategy, and selective disclosure built to reduce exchange friction and support institutional workflows, without abandoning the cryptographic integrity expected of modern ZK systems.
Presale note
A short campaign update: the $NOC presale is scheduled to start on January 20th.
https://noc-tura.io/?from=article-links?from=article-links
https://noc-tura.io/?from=article-links?from=article-linkswhitepaper.pdf
Disclaimer: This is sponsored content. The information on this page is not endorsed or supported by U.Today, and U.Today is not responsible or liable for any inaccuracies, poor quality, advertising, products or other materials found within the publication. Readers should do their own research before taking any actions related to the company. U.Today is not responsible, directly or indirectly, for any damage or loss caused or alleged to be caused by or in connection with the use of or reliance on any content, goods or services mentioned in the article.

 Dan Burgin
Dan Burgin Vladislav Sopov
Vladislav Sopov